Signing launchers and installers
2009-04-22
Posted by Hannes Kegel
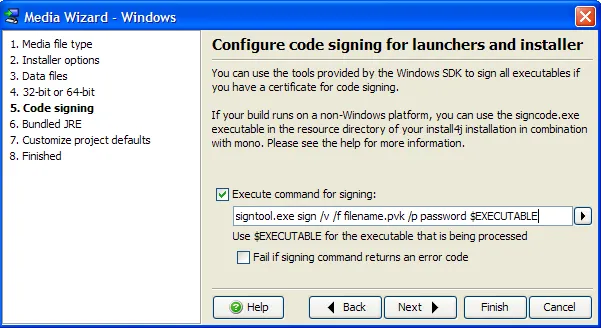
install4j provides a signing hook for all generated windows executables. On step 5 of the Windows Media Wizard, you can specify any external tool with the executable files as parameter. The signing tool will be called with the working directory set to the project file parent directory so you can specify keys and certificates relatively. You can use the
$EXECTUABLE
variable to refer to the launcher or installer and an $OUTFILE
variable if the tool you use requires different in and out files.
I will explain below what tools you can use to sign your executables, but first, you would need a Microsoft Authenticode Certificate from a certificate authority like Thawte:
https://www.thawte.com/code-signing/index.html
In their order process, they will generate a private key (PVK) file and a certificate request. After Thawte verified your identify, they will provide you a SPC file that contains your certificate. There are a bunch of other certificate authorities, most notably verisign where the process is quite similar.
Code signing on Windows
On Windows, you can quite easily use Microsoft's tools like signcode or signtool which are contained in the freely available Platform and .Net SDKs. You can find the documentation in the MSDN:
http://msdn.microsoft.com/de-de/library/9sh96ycy%28VS.80%29.aspx
Below is a good summary of how to use signtool:
http://www.curlybrace.com/words/2008/09/12/using-certificates-and-signtool/
It also explains how to convert different file formats that other certificate authorities might issue.
Code signing on other platforms with Mono's signcode
It is also possible to sign executables on other platforms. The
$INSTALL4J_HOME/resource/signcode.exe
executable is a mono
executable modified by ej-technologies to support signing of 64-bit executables. This executable can only be executed if
mono is installed. Mono is available for a number of platforms and can be downloaded free of charge.
The tool has the same syntax as the one from Microsoft. A typical entry would be
mono /opt/install4j/resource/signcode.exe -spc mycert.spc -v mykey.pvk -vp password -t http://timestamp.verisign.com/scripts/timstamp.dll $EXECUTABLESome SPC files cannot be read directly by this tool. If this is the case for your certificate, you can export all CER files from the SPC file and generate a new SPC file with the
cert2spc
tool included with mono. You have to add the CER files in the order of the certificate chain (your own certificate is
the last one on the command line).
Code signing on other platforms with openssl and osslsigncode
Here is a download with a patch for signing PE32+ (Windows x64) executables. A short
./configure && make
should be sufficient when you have curl and openssl installed. This tool requires the private key in a different form,
though. First, you would have to convert your PVK file to a PEM file with this tool
on Windows. A typical command line would be simply
pvk -in mykey.pvk -out mykey.pem.
The upcoming openssl 1.0 will also be able to do this conversion. The PEM file is still encrypted, but osslsigncode needs an unencrypted DER file. You might want to generate this DER file directly before your build process and delete it afterwards to avoid having your private key hanging around unencrypted longer than necessary. The conversion to a DER file is done with
openssl rsa -passin pass:XXXXX -outform der -in mykey.pem -out mykey.der.
A typcial command line in install4j would then be
osslsigncode -spc mycert.spc -key mykey.der -t http://timestamp.verisign.com/scripts/timstamp.dll -in $EXECUTABLE -out $OUTFILE.
Remember that the spc and key files can be specified relatively to your install4j project file.
Update: As of install4j 5.1, code signing is implemented directly and the above mentioned tools are no longer required.
Archive
October/1
August/1
July/2
2024/5
2023/7
The power of async tracking in JVM profilingWebsite refresh: Visual updates, dark mode, and semantic search for docs
June/4
All our artifacts are now published on Maven CentralJEP 493 follow-up: install4j 11.0.4 is ready for separate JMOD bundles in Eclipse Temurin 24.0.2JProfiler tips roundup May 2025JVM performance watch roundup May 2025
May/3
JProfiler tips roundup April 2025JVM performance watch roundup April 2025Heap Walker scripting for snapshot analysis
April/8
Capturing and comparing MBean states with JProfilerAdvanced SSH remote profiling with JProfilerProfiling Java applications in VS Code with JProfilerAdvanced Kafka probe configuration in JProfilerProfiling Kafka #1 – Message Flow & Hot SpotsBringing JProfiler to VS Code with Kotlin Multi-PlatformCaching auto-provisioned install4j distributions in CI pipelinesCross-platform JRE bundle creation under threat from JEP 493
January/1
September/5
2022/10
Garbage collector analysis in JProfilerRecording JFR snapshots with JProfilerEnhanced JFR snapshot analysis with JProfilerWorking with probe events in JProfilerCustomizing telemetries in JProfiler
March/1
January/1
December/2
November/3
2021/2
2020/1
2019/1
2018/3
2017/5
2016/1
2015/10
Using sunburst diagrams for understanding Java memory consumptionUsing flame graphs when profiling Java applicationsProfiling a Netty server
October/1
September/1
August/2
July/1
November/5
2014/3
2013/3
2012/5
2011/13
Analyzing specific parts of the call treeAnalyzing incoming and outgoing calls of a methodCollapsing recursions in the call treeRemote profiling through an SSH tunnelFinding JDBC connection leaks
June/5
December/1
October/2
September/5
2010/8
2009/14
Using the "Run interceptor script" trigger actionCreating a custom probeInspections in the heap walkerHeap walker graph: Finding paths between selected instancesFiltering in the reference view of the heap walker
August/4
Request trackingAnalyzing long-running AWT events with JProfilerProbes overviewCPU profiling: Sampling and instrumentation
February/1